Managing Default Access Policies
Default Access Policies are the security policies that are applied by default to each of the components in a registry. These are the base permissions that get assigned to an entity when it is created--if that component does not automatically inherit its permissions from another component. Any component-level permissions that are added or changed from the Sharing or Security tabs in the Anzo application supersede the default access policy.
| Note | Default access policies only apply to components that have no other access control logic added at creation time. To facilitate common workflows, when a component is created using the Anzo user interface the application applies logic so that all of the components in the workflow inherit the same permissions. For example, when the Ingest workflow is used to onboard data from a data source, the resulting model, pipeline, and mapping components inherit permissions from the data source by default. And when a pipeline is published, the resulting file-based linked data set inherits permissions from the pipeline. Because of permission inheritance, default access policies are rarely applied to new components and typically are not changed. |
This topic describes the default access policies for each registry and provides instructions for changing access policies.
- Default Access Policy Permissions Reference
- Default Access Policy Registry Reference
- Configuring Default Access Policy Permissions
Default Access Policy Permissions Reference
Default access policies use the same predefined permission sets and mechanism for assigning permissions as other components in the Anzo application, such as graphmart and data source sharing. There are three predefined permission sets that include a combination of six permissions that can be assigned to the creator of the component and other Anzo users, groups, or roles.
The table below lists the predefined permission sets and describes the privileges that are granted for each permission that is part of the predefined set:
Default Access Policy Registry Reference
There is a default access policy for each of the Anzo registries. A registry is a system-level collection of application and system component configurations of the same type, such as graphmarts, data sources, ontologies, roles, etc. Like data, registries are stored and managed as RDF named graphs according to ontologies. Each registry is a Linked Data Set.
| Important | Never modify any of the Anzo registries. Changing or removing a registry can irreparably damage your Anzo server. |
To see and manage the default access policies, expand the Administration menu and click Default Access Policies. The sections below provide details about each of the registries for which you can configure default access policies:
- Data Sources Registry
- Global Linked Data Config
- LinkedDataSets Collection Catalog
- Elastic Search Configuration Registry
- Ontology Registry
- Role Registry
- Graphmarts Registry
- Datasets Registry
- Favorites Registry
- Comments Registry
- Linked Data Set Registry
- Persisted Queries Registry
Data Sources Registry
| Item | Description |
|---|---|
| Data Sources Registry and Policy | This registry is the collection of all data source configurations. This access policy is applied by default when a data source is created. |
| Default Access Configuration | Creator: Admin Everyone: View |
| Default Access Details | The Creator of a data source is assigned the Admin permission set for that data source. The Everyone role is assigned the View permission set. |
Global Linked Data Config
| Item | Description |
|---|---|
| Global Linked Data Config Registry and Policy | This registry is a catch-all for system settings that are related to URIs, including URI prefixes and the base URI (such as csi.com for class instance URIs), as well as other specifics about entities that are created in Anzo. This registry also supplies the default ACL configuration for components if nothing else applies. |
| Default Access Configuration | Creator: Modify |
| Default Access Details | The Creator of a component that follows this policy is assigned theModify permission set. |
LinkedDataSets Collection Catalog
| Item | Description |
|---|---|
| LinkedDataSets Collection Catalog Registry and Policy | This is a legacy registry that stores Linked Dataset Collection configuration data. Linked dataset collections were the precursor to graphmarts and have been deprecated in most organizations. If you do use linked dataset collections, this access policy is applied by default when a new collection is created. |
| Default Access Configuration | Creator: Admin Everyone: View |
| Default Access Details | The Creator of a linked dataset collection is assigned the Admin permission set for that collection. The Everyone role is assigned the View permission set. |
Elastic Search Configuration Registry
| Item | Description |
|---|---|
| Elastic Search Configuration Registry and Policy | This registry is the collection of all Elasticsearch connection configurations. This access policy is applied by default when an Elasticsearch connection is created. |
| Default Access Configuration | Creator: Admin Everyone: View |
| Default Access Details | The Creator of an Elasticsearch connection is assigned the Admin permission set for that configuration. The Everyone role is assigned the View permission set. |
Ontology Registry
| Item | Description |
|---|---|
| Ontology Registry and Policy | This registry is the collection of all ontology configurations. This access policy is applied by default if a model is created and no other access control logic is applied. |
| Default Access Configuration | Creator: Admin Everyone: View |
| Default Access Details | The Creator of a data model is assigned the Admin permission set for that model. The Everyone role is assigned the View permission set. |
Role Registry
| Item | Description |
|---|---|
| Role Registry and Policy | This registry is the collection of all role configurations. This access policy is applied by default when a role is created. |
| Default Access Configuration | System Administrator: Admin Everyone: View |
| Default Access Details | The System Administrator is assigned the Admin permission set and is the only user who can create roles. The Everyone role is assigned the View permission set. |
Graphmarts Registry
| Item | Description |
|---|---|
| Graphmarts Registry and Policy | This registry stores all graphmart configurations. This access policy is applied by default if a graphmart is created and no other access control logic is applied. |
| Default Access Configuration | Creator: Admin Everyone: View |
| Default Access Details | The Creator of a graphmart is assigned the Admin permission set for that graphmart. The Everyone role is assigned the View permission set. |
Datasets Registry
| Item | Description |
|---|---|
| Datasets Registry and Policy | This legacy registry stores configurations for non-ontology-backed data sets. This registry is not used; there is nothing that can be created in the user interface that affects this registry. |
| Default Access Configuration | N/A |
| Default Access Details | N/A |
Favorites Registry
| Item | Description |
|---|---|
| Favorites Registry and Policy | This registry stores configurations for components that have been tagged as favorites. The access policy applies by default when a component is marked as a favorite. |
| Default Access Configuration | Creator: Admin |
| Default Access Details | The user who tags a component as a favorite is assigned the Admin permission set. Favorites are unique to each user, and a user cannot see another user's favorites. |
Comments Registry
| Item | Description |
|---|---|
| Comments Registry and Policy | This registry stores configurations for comments that have been added to components. The access policy applies by default to new comments. |
| Default Access Configuration | Creator: Admin Everyone: View |
| Default Access Details | The Creator of a comment is assigned the Admin permission set for that comment. The Everyone role is assigned the View permission set, which means they can see the comment but not change or remove it. |
Linked Data Set Registry
| Item | Description |
|---|---|
| Linked Data Set Registry and Policy | This registry stores configuration information for all linked data sets, notably the file-based linked data sets that are listed on the Datasets screen in the Anzo application and are available to add to graphmarts. |
| Default Access Configuration | N/A |
| Default Access Details | File-based linked data sets (FLDS) in the Linked Data Set Registry inherit their permissions from the components that make up the FLDS. |
Persisted Queries Registry
| Item | Description |
|---|---|
| Persisted Queries Registry and Policy | This registry stores configuration information for all of the saved queries in the Query Builder. This access policy is applied by default when a new query is saved. |
| Default Access Configuration | Creator: Admin |
| Default Access Details | The user who saves a query is assigned the Admin permission set. By default, saved queries are unique to each creator, and other users cannot see another user's queries. |
Configuring Default Access Policy Permissions
Follow the instructions below to change the default access policy for a registry.
| Important | Changing default access control policies does not change permissions on any existing components. The changes affect only new components that are created after the change and if no other permission inheritance logic applies. Because of permission inheritance, default access policies are rarely applied to new components and typically are not changed. |
- In the Anzo application, expand the Administration menu and click Default Access Policies. The Default Access Policies screen is displayed.
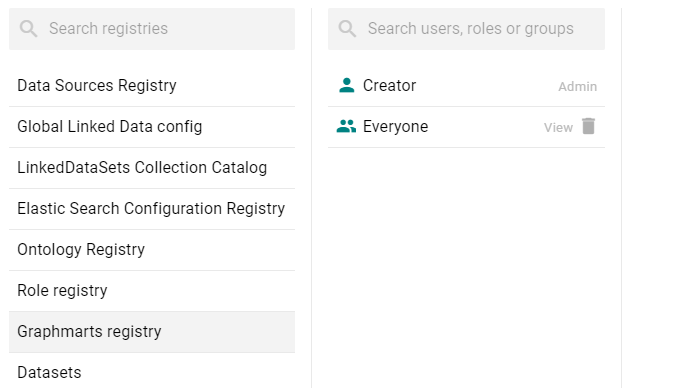
- On the left side of the screen, select the access policy that you want to configure. The current configuration for that policy is shown on the right side of the screen. For example, the image below shows the Graphmarts Registry. The graphmart Creator has Admin permissions, and the Everyone role has View permissions.
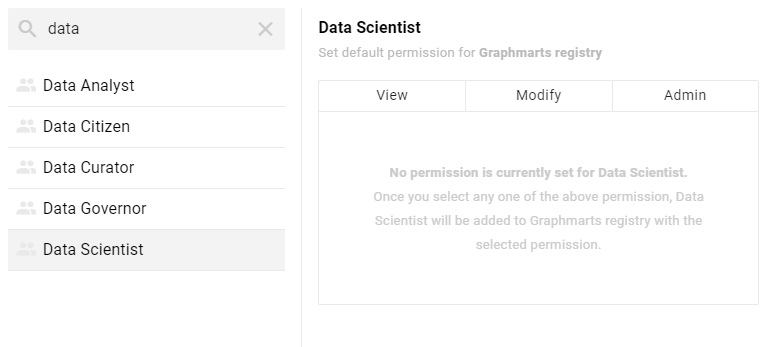
- To change a configured user, group, or role, select a name in the list to view the permissions on the right side of the screen. To add a user, role, or group to configure, type a term in the Search field. Then select a name in the result list to view the permissions details. For example, the image below shows the search results for additional roles and selects the Data Scientist role:
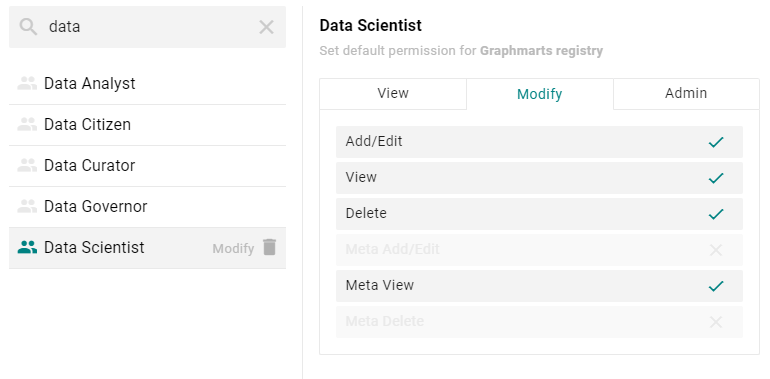
- On the right side of the screen, click the tab for the predefined permission set that you want to assign to the selected user, group, or role. For information about the permission sets, see Default Access Policy Permissions Reference above. For example, the image below assigns the Modify permission set to the Data Scientist role.
To clear permissions for a user, role, or group, click the trashcan icon (
 ) next to the user, role, or group name.
) next to the user, role, or group name. - To configure additional users, groups, or roles, select the name and then repeat the step above to apply a permission set. Changes to access control policies are automatically saved.