Adding a SAML Provider
Follow the steps below to add a SAML SSO Provider.
- In the Administration application, expand User Management and click SSO Config. Anzo displays the Single Sign On screen, which lists any existing providers. For example:
- Click the Add SSO Config button and select SAML Provider. The Create SAML Provider screen is displayed.
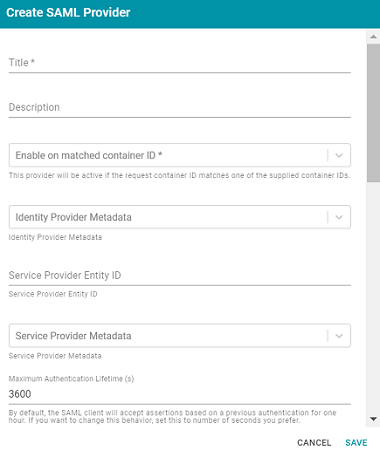
- Configure the required properties and any optional settings as needed. The list below describes the properties.
- Title: This property sets the name for the connection that you are creating.
- Description: This property can be used to provide a brief description of the provider configuration.
- Enable on matched container ID: This property sets the list of container IDs to match. This provider will be active if the request container ID matches one of the listed container IDs. Click the field and select a container ID from the drop-down list. To specify multiple IDs, click the field again and select another value. To remove a container from the list, click the X on the right of the container name.
- Identity Provider Metadata: This property can be used to include the identity provider metadata .xml file. To add the file, click the field and then click Add File to select the file.
- Service Provider Entity ID: This property can be used to identify the service provider to the identity provider during the SSO process. The entity ID is a unique identifier for the service provider, typically a URL that points to the service provider’s metadata.
- Service Provider Metadata: This property can be used to include the server provider metadata .xml file. To add the file, click the field and then click Add File to select the file.
- Authentication Request Binding: This property can be used to specify the redirect binding that the service provider should use to pass an authentication request to the identity provider.
- Maximum Authentication Lifetime (seconds): This property can be used to adjust the amount of time the authentication spans. By default, the SAML client accepts assertions for one hour based on a previous authentication. To change the lifetime, you can set this property to the desired number of seconds.
- Enable on login page: This property controls whether to display a link for this provider on the Anzo login screen.
- Callback URL: This property specifies the URL that the provider should use to redirect users back to the Anzo application after a successful login. Include the full URL to the Anzo instance, through the proxy if one exists. Specify the URL in quotes and append the value with
/anzo_authenticate, i.e.,"hostname:port/anzo_authenticate". - Callback URL port replacement: This property can be used to define the port to use if the one specified in the
Callback URLfield is unavailable. - User Identifier: This property specifies the SSO provider attribute, such as
emailorusername, to use for looking up users in the directory server. - IDP Logout Capable: This property can be used to indicate whether the SSO provider supports logging the user out of the IDP when they log out of Anzo.
- Default to IDP Logout: This property controls whether to log a user out of the IDP by default when they log out of Anzo.
- Logout URL Suffix: When
Default to IDP Logoutis enabled, this property can be used to specify the logout URL for the SSO provider. The[urlAfterLogout]placeholder is replaced with the SSO provider server URL. - Email Template regex: If an email attribute was specified as the User Identifier, this property can be used to specify a regular expression to use for identifying variations between email addresses stored by the SSO provider and email addresses returned by the directory server.
- Email Template Replacement: This property can be used to define a replacement email template to use if there are variations found by
Email Template regex. - User Template regex: If a username attribute was specified as the User Identifier, this property can be used to specify a regular expression to use for identifying variations between user names stored by the SSO provider and names returned by the directory server.
- User Template Replacement: This property can be used to define a replacement user template to use if there are variations found by
User Template regex. - Use username directly: This property controls whether the identity provider directly authenticates a user by validating a username and password or by validating an assertion about the user’s identity as defined by a separate identity provider.
- Skip CSRF check: This property controls whether to perform or skip a cross-site request forgery (CSRF) check.
- LDAP domain: This property identifies the LDAP domain to use for user lookup.
- LDAP email property: This property defines the LDAP email property to use to find the associated user's dn. For example,
http://openanzo.org/ontologies/2008/07/Anzo#ldapEmailInfo. - Principal Template: This property can be used to define the template to use for populating roles and returning user URIs.
- Icon: This property can be used to include an SSO icon on the Anzo login screen. To select an image, click the Icon field and select Add File.
- With State: This property controls whether information about the application's state is included in authentication requests.
- When you have finished configuring properties, click Save to save the provider setup.