Configure AnzoGraph DB for LDAP Authentication
By default, the AnzoGraph DB front end console is configured to use authentication and authorization credentials maintained by AnzoGraph DB itself. You can also configure the AnzoGraph DB front end console to use a specified LDAP or directory service to authenticate users and authorize AnzoGraph DB operations based on user membership in LDAP groups. See Create and Manage Roles from the Console for information on creating uer roles and granting or revoking permissions to access specific AnzoGraph DB database objects (graphs, views, and queries), whether you are using local AnzoGraph DB or LDAP service authentication of users.
Define an LDAP Configuration
To configure the AnzoGraph DB front end console and AnzoGraph DB to use LDAP authentication:
- Select LDAP Configuration from the Server Settings list to display the LDAP Configuration screen.
- On the LDAP Configuration screen, configure the connection to your AnzoGraph DB deployment by selecting the Enable LDAP Authentication checkbox and then choosing among the various radio button options and supplying values for the required fields.
Selecting the Enable LDAP Authentication checkbox enables front end authentication using the the LDAP configuration.
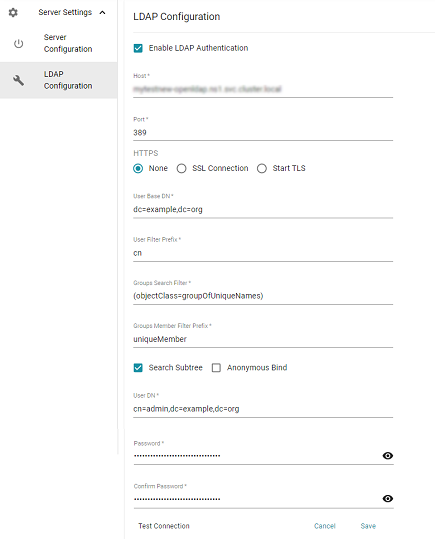
Field entries for the LDAP Configuration are the following:
- Enable LDAP Authentication checkbox: Selection that allows you to enable front end authentication using the LDAP configuration.
- Host: Host name or IP address of the LDAP directory server.
- Port: The port used to connect to the LDAP directory server.
- HTTPS radio buttons: Specifies whether the directory server uses an SSL (LDAPS) or a StartTLS protocol connection.
- User Base DN: LDAP distinguished name that contains users than can be authenticated, for example:
dc=example,dc=org. - User Filter Prefix: Property name that a user name is mapped to, for example:
cn. - Groups Search Filter: Filter used to search for LDAP group names, for example:
(objectClass=groupOfUniqueNames). - Groups Member Filter Prefix: Property name prefix used for searching if user is part of group, for example:
uniqueMember. - Search Subtree checkbox: Option to specify whether to search LDAP subtrees.
- Anonymous Bind checkbox: Option to specify whether the AnzoGraph DB front end console connects to the directory server anonymously.
- User DN: Full distinguished name of the account that the AnzoGraph DB front end console will bind against to perform authentication on the directory server, for example:
cn=admin,dc=example,dc=org. - Password: Password specified for the User DN.
- When you have supplied all of the necessary connection details, click Test Connection at the bottom of the screen to ensure that the connection with your LDAP directory service can be made.
If the test fails, adjust the values as needed and test the connection again.
- Click Save to save the connection.
Enable LDAP Authentication for the Console
To use an LDAP configuration to authenticate Console login and authorize AnzoGraph DB operations users are able to perform, you need to update settings in the AnzoGraph DB settings.conf configuration file. That is, to enable external LDAP authentication to the console, you need to configure the following options in the AnzoGraph DB settings.conf file (located in the InstallDir/anzograph/config directory) :
enable_acl=true enable_external_auth=true
After updating the settings in the AnzoGraph DB configuration file, you need to restart AnzoGraph DB for the new settings to take effect. For example:
<install_path>/anzograph/bin/azgctl -restart
With these new ACL settings, AnzoGraph DB front end console users will be authenticated against an externally- configured LDAP directory service. A user's LDAP group membership information will be passed to AnzoGraph DB along with any submitted SPARQL query request or statement they submit to help in authorizing requests. Where AnzoGraph DB roles are already defined that match the names of LDAP groups a user is a member of, the AnzoGraph DB assigned role permissions will determine a user's authorization or permission to execute any submitted SPARQL request.
See Access Control Basics and Terminology for more information on AnzoGraph DB ACL operations and additional methods of integrating LDAP directory services with AnzoGraph DB.
You can now use the front end console using LDAP directory service authentication of users. For more information on using the front end console, see Use the Query & Admin Console. Also refer to Create and Manage Roles from the Console for information on defining or updating roles that control Console user access and permissions.