AWS CloudFormation Deployment Infrastructure Options
This topic describes the deployed AnzoGraph DB cloud architecture and details the three AWS CloudFormation deployment scenarios or use cases that are presented on the AnzoGraph DB launch page. The use cases correspond with commonly used AWS network and environment configurations. Select one of the following options to view details about the particular use case you want to deploy.
- Deploy AnzoGraph in an Existing Public Subnet with Restricted Access
- Deploy AnzoGraph in a Private VPC Subnet
- Deploy AnzoGraph as SaaS using AWS PrivateLink
This deployment scenario deploys AnzoGraph DB in a public subnet and secures the environment by limiting access to specific address spaces (CIDRs). The instructions in Deploy AnzoGraph with Restricted Access provide details about how to secure the environment by limiting access to specific CIDRs.
In this scenario:
- You create a VPC with a public subnet as described in Creating a VPC. When you run the AnzoGraph DB CloudFormation wizard to launch AnzoGraph DB, you select this VPC and its subnet. For more information about VPCs, see What Is Amazon VPC? in the AWS documentation.
- You select the public subnet that you created with your VPC and the CloudFormation wizard deploys AnzoGraph DB into it. The subnet is the range of IP addresses in the VPC that is reserved for certain resources. For more information about subnets, see VPCs and Subnets in the AWS documentation.
- You restrict AnzoGraph DB access to specific address spaces by specifying the classless inter-domain routing (CIDR) addresses to allow. The CloudFormation wizard creates a security group based on the AnzoGraph DB requirements, VPC and subnet configuration, and the CIDRs that you specify. For more information about security groups, see Amazon EC2 Security Groups for Linux Instances in the AWS documentation.
- You select the number of nodes to include in the AnzoGraph DB cluster, and the CloudFormation wizard deploys one instance as the leader node and the rest as compute nodes.
- AnzoGraph DB has access to the internet and data load files stored in locations like Amazon S3 (in any region) or a web server.
- If you use NFS servers to store data, the CloudFormation wizard enables you to specify a list of the servers and automatically mounts the directories to each of the AnzoGraph DB nodes.
The diagram below shows the deployed AnzoGraph DB cloud environment in this scenario.
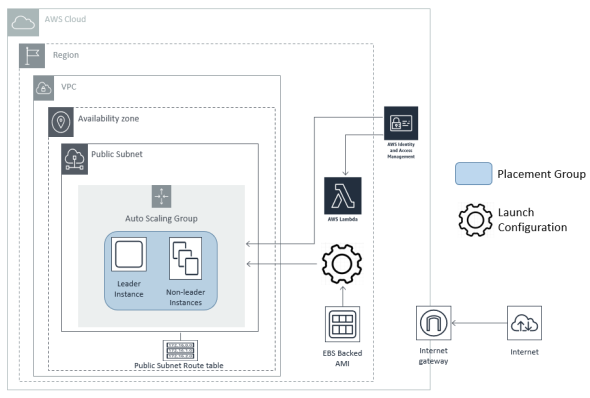
The Cambridge Semantics CloudFormation service manages all resources that it creates. When you delete an AnzoGraph DB stack, all CloudFormation-managed resources are also deleted. The CloudFormation does not remove or alter your existing components.
This deployment scenario lets you to take advantage of the ease and speed of the fully automated deployment combined with the security of your existing AWS intranet setup.
In this scenario:
- You have an Amazon Virtual Private Cloud (VPC) with iBGP routing access to the intranet. The Cambridge Semantics CloudFormation service supports AWS VPN and AWS Direct Connect uplinks.
- You have an existing subnet that is configured with internet (outbound) and intranet access or a NAT-enabled subnet that routes through an existing NAT gateway.
- The CloudFormation wizard deploys AnzoGraph DB clusters into the existing VPC.
- The CloudFormation wizard creates new security groups based on your VPC and subnet configuration and AnzoGraph DB requirements.
- If you use NFS servers to store data, the CloudFormation wizard enables you to specify a list of the servers and automatically mounts the directories to each of the AnzoGraph DB nodes.
- The AnzoGraph DB cluster is accessible only from within the intranet and/or any networks that you specify during the deployment.
When deploying the AnzoGraph DB infrastructure, you specify the classless inter-domain routing (CIDRs) that are permitted to access AnzoGraph DB. For example, if the intranet uses the 10.0.0.0/8 address space, you can specify the CIDR 10.0.0.0/8 to allow all IP addresses in the intranet to access AnzoGraph DB. Or you can specify a list of CIDRs to enable more restrictive access. For example, you could specify 10.0.3.0/24, 10.0.4.0/8.
The CloudFormation wizard creates the appropriate subnet in the VPC to host the AnzoGraph DB cluster. If necessary, it also provides a network address translation (NAT) gateway that enables outbound traffic between the instances in your private subnet and the internet or other AWS services. Since the traffic is outbound only, NAT gateways prevent the internet or other services from initiating a connection to your instances and enable AnzoGraph DB to securely access data load files stored in locations such as on Amazon S3 (in any region), a web server, or a Google Cloud Storage Bucket. For more information about NAT gateways, see NAT Gateways in the AWS documentation.
The diagram below shows the deployed AnzoGraph DB cloud environment in this scenario.
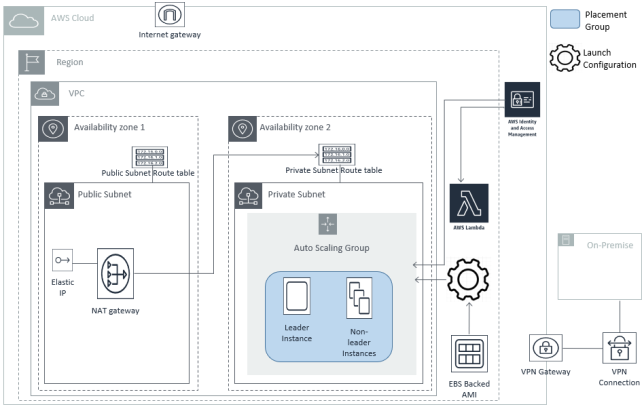
The Cambridge Semantics CloudFormation service manages all resources that it creates. When you delete an AnzoGraph DB stack, all CloudFormation-managed resources are also deleted. The CloudFormation does not remove or alter your existing components.
This use case describes a scenario where the Cambridge Semantics CloudFormation service automatically deploys a secure, isolated AnzoGraph DB environment that is based on AWS PrivateLink. The CloudFormation service deploys all of the AWS infrastructure that hosts AnzoGraph DB and configures a VPC endpoint service that enables you to access the AnzoGraph DB endpoint from other AWS Virtual Private Cloud (VPC) environments in the same region.
In this scenario:
- The CloudFormation deployment requires very little input from users. You do not need to set up or specify an existing VPC or subnet. The CloudFormation service creates all of the AWS infrastructure needed to enable access to AnzoGraph DB as an endpoint service:
- The service creates a new VPC in the region that you specify.
- The service creates a new security group to manage inbound and outbound traffic for the VPC.
- The service creates subnets in the VPC to reserve ranges of IP address for AnzoGraph DB and the NAT gateway.
- The service deploys a private network load balancer to act as a TCP forwarder to AnzoGraph DB
- The service deploys a PrivateLink endpoint service to enable the connection between AnzoGraph DB and other VPCs or AWS services.
- You set up an endpoint service for each VPC that needs access to the AnzoGraph DB endpoint. For more information, see Whitelist Principals and Create a VPC Endpoint.
The diagram below shows the deployed AnzoGraph DB cloud environment in this scenario.
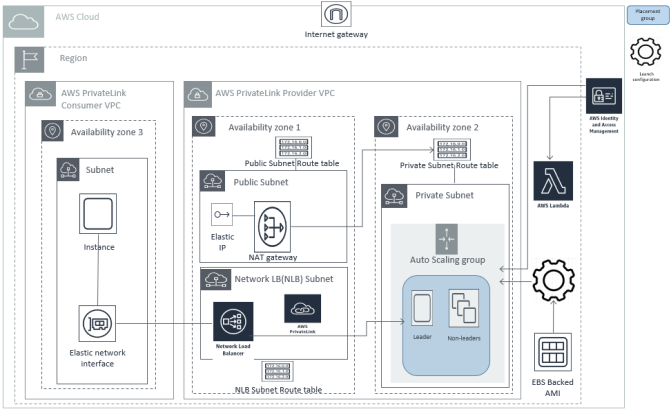
The Cambridge Semantics CloudFormation service manages all resources that it creates. When you delete an AnzoGraph DB stack, all CloudFormation-managed resources are also deleted. The CloudFormation does not remove or alter your existing components.