Artifact Access Control Concepts
The implementation of artifact and data access control in Anzo is an aggregation of three mechanisms:
- Default Access Policies: These are the base permissions that are applied to artifacts by default when they are created. For most types of artifacts, the access control that is supplied by a Default Access Policy is augmented by the other two access control mechanisms.
- Permission Inheritance: To facilitate common workflows, the Anzo application applies logic so that artifacts in the same workflow inherit the same permissions. For example, when a user creates a Data Source and uses the Ingest workflow to onboard the data, the generated Model, Pipeline, and Mapping artifacts inherit their permissions from the Data Source. Once the pipeline is published, the resulting Dataset inherits the permissions from the Pipeline. This permission inheritance is applied in addition to the applicable Default Access Policy.
- Sharing: An artifact's creator can also share access to their artifact with other users or groups. When an artifact is shared, those user-configured permissions are applied in addition to any permissions that were inherited.
The following diagram illustrates the above concepts. Details about the processes and components depicted in the diagram are provided in the sections below.
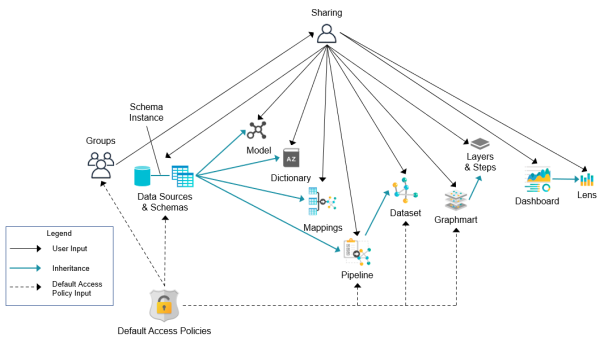
Default Access Policies
Default Access Policies are the security policies that are applied by default to the artifacts that belong to a particular system registry (see Registries below). Default Access Policies are the base permissions that get assigned when an artifact is created—before any other access control logic (e.g., Permission Inheritance) is applied. Any artifact-level logic that is applied by Anzo or configured from the Sharing tab in the Anzo application augments the permissions that were supplied by the Default Access Policy.
For more information about Default Access Policies, see the following topic:
Registries
A registry is a system-level graph that stores metadata about artifacts of the same type. For example, a Data Sources Registry stores metadata about all of the Data Source and Schema artifacts, and an Ontology Registry stores metadata about all of the Data Model artifacts. Like onboarded data, registries are stored and managed as RDF named graphs according to system ontologies.
Aside from changing the Default Access Policy for a registry, do not make additional modifications to registries. Changing or removing a registry can irreparably damage your Anzo server.
Permission Inheritance
The concept of inheritance is fundamental to the implementation of access control in Anzo. Inheritance allows related entities to share permissions with each other, making access easier to manage collectively, and ensuring that users have the appropriate access to each of the dependent artifacts that are crucial to their workflow. The following subsections describe the relationships and inheritance rules for each type of artifact.
- Data Sources & Schemas
- Ingest Workflow
- Graphmarts
- Structured Pipelines
- Unstructured Pipelines
- Metadata Dictionaries
- Users and Roles
- Role Permissions and Registries
Data Sources & Schemas
Data Sources and Schemas have a fundamental relationship since Schemas are imported from Data Sources and, in a sense, belong to them. Because a Data Source can have more than one Schema and the Schemas can be managed independently, Data Sources and Schemas exist as separate artifacts in Anzo. However, because of their implicit relationship, Anzo uses inheritance to facilitate users' interaction with Data Sources and the Schemas created from them.
If Anzo did not apply inheritance, a user who shares a Data Source would have to remember to add the new user to the data source and navigate to each related schema and add the new user there as well. Keeping permissions in sync manually presents a big challenge that is curtailed by applying inheritance.
To summarize the inheritance rules for Data sources and Schemas:
- Schemas inherit from the Data Source from which they were imported.
- Schema instances, which link Schemas to their Data Source, inherit from both the Schema and the Data Source.
Ingest Workflow
A primary workflow in Anzo is to create a new data source and then use the Ingest workflow (sometimes referred to as "auto-ingest") to generate all of the artifacts that are needed onboard the data and create the corresponding graph Dataset in Anzo. Artifacts created from the Ingest workflow inherit their permissions from the original Data Source.
If Anzo did not apply this inheritance, a user who wanted to share the Dataset that was derived from a Data Source would need to manually edit permissions for every artifact in the workflow: Model, Mappings, and Pipeline.
To summarize the inheritance rules for the Ingest workflow:
- Models generated by the Ingest workflow inherit permissions from the Data Source.
- Mappings generated by the Ingest workflow inherit permissions from the Data Source.
- Pipelines generated by the Ingest workflow inherit permissions from the Data Source.
In rare cases when inheritance rules do not apply to artifacts, such as if a user manually creates a Mapping outside of the Ingest workflow, the SDI Registry Default Access Policy would supply the permissions for that Mapping until permissions are configured from the Mapping's Sharing tab.
Graphmarts
When a user creates a Graphmart, the Graphmart is assigned permissions according to the Graphmarts Registry Default Access Policy. Graphmarts contain Data Layers that describe and group the transformations that take place as the knowledge graph is generated. Since Data Layers are created in the context of a Graphmart, they inherit their permissions from the Graphmart by default.
If Anzo did not apply this inheritance, a user who wanted to share a Graphmart would have to remember to configure each newly created Data Layer to assign permissions that match the Graphmart's permissions. Otherwise someone who had access to the Graphmart would not be able to view or edit its layers and steps.
To summarize the inheritance rules for Graphmarts:
- Graphmarts inherit permissions from the Graphmarts Registry Default Access Policy.
- Data Layers and Steps created in a Graphmart inherit from the Graphmart.
For more information about graphmart permissions, see Sharing Access to Graphmarts.
Structured Pipelines
When a Structured Pipeline is published, it creates a Dataset. Since the most common data ingestion workflow is for a user to introduce a Data Source and then ingest the data into a Dataset by running a Pipeline, Datasets created from a Pipeline inherit their permissions from the Pipeline. If Anzo did not apply this inheritance, a user who has access to a Pipeline might lose the ability to see its output if the Pipeline happened to have been run by someone else first, for example.
To summarize the inheritance rules for Structured Pipelines:
- Datasets created from Structured Pipeline runs inherit from the Pipeline.
- Datasets created from auto-generated structured pipelines inherit from the original Data Source that was used to generate the Structured Pipeline.
Unstructured Pipelines
As with structured pipelines, running an Unstructured Pipeline produces a Dataset. For similar reasons, the output unstructured Dataset inherits from the Unstructured Pipeline. Additionally, each Unstructured Pipeline run produces a status dataset that is specific to the pipeline's execution. Since these status datasets are implicitly related to the Unstructured Pipeline, they inherit permissions from the pipeline.
To summarize the inheritance rules for Unstructured Pipelines:
- Datasets created from Unstructured Pipeline runs inherit from the corresponding Unstructured Pipeline.
- Pipeline status datasets inherit from the related unstructured pipeline. From an end user's perspective, this relates to the status information that is displayed in the Unstructured Pipeline user interface.
Metadata Dictionaries
Users can create Metadata Dictionaries from specific Data Sources. Because the dictionary is directly related to the origin Data Source, Metadata Dictionaries inherit their permissions from the corresponding Data Source. If one dictionary is used for multiple sources, the dictionary inherits the superset of permissions from the origin Data Sources.
To summarize the inheritance rules for Metadata Dictionaries:
- Dictionaries generated from Data Sources inherit permissions from the Data Source.
- Dictionaries that link concepts from multiple Data Sources inherit from all corresponding Data Sources.
Users and Roles
Users and roles are typically managed by administrators as a collective group. There are not clear use cases for a given user to manage some user and role accounts but not others. The expectation is that users who have the Manage Users, Groups, and Roles permission should be able to manage all users and roles, not just a subset of them.
To accomplish the above expectation, all users inherit permissions from one system registry, the Role and Permissions Registry. If user and role permissions were not centralized, there could be circumstances where one user creates a new user or role in Anzo and other users cannot see or edit that account even if they belong to a role that has the Manage Users, Groups, and Roles permission. Also if the original user or role creator had the Manage Users, Groups, and Roles permission revoked, they may retain control over the accounts they created when they had the ability to do so.
To summarize the inheritance rules for users and roles:
- Anyone who has the Manage Users, Groups, and Roles permission has the Admin level of access to all users, groups, and roles.
- The Everyone role has View access to all users, groups, and roles so that they can share artifacts with other users and groups.
Role Permissions and Registries
Access to certain registries is mapped to specific Anzo permissions. This is helpful when artifacts that are added to a registry inherit their permissions from the registry itself rather than another artifact, such as with Users and Roles. When users have a permission that grants them access to a registry, that means they can see all artifacts that belong to that registry.
The list below describes the registry access that is controlled by a permission.
- Access to the Role and Permissions Registry is granted by the Manage Users, Groups, and Role permission.
For more information about the Anzo permissions, see Role Permissions Reference.
Sharing
Artifacts can be shared with other users and groups from the artifact's Sharing tab in the Anzo application. When an artifact is shared, those user-defined permissions are added to the set of permissions that came from the Default Access Policy for the related registry as well as the permission inheritance that is applied by Anzo.
For details about artifact sharing, see Sharing Access to Artifacts.