User Management Concepts
Typically organizations connect Anzo to their central directory server and then add users and groups from the server to Anzo. Once the accounts are added to Anzo, access control is managed in two ways:
- Groups (or users) are added to Roles and the roles are configured to grant access to functionality in Anzo. Role permissions grant access to menus and screens in the Anzo and Administration applications. Access to functionality cannot be assigned to groups or users, only to roles.
- Groups and users are used to control access to individual artifacts—Project's Data Sources, Models, Mappings, Pipelines, Graphmarts, etc.—and your data that is stored in Anzo.
Though Anzo is flexible and allows you to assign artifact access to roles, the recommendation is to control access to artifacts with users and groups and reserve roles for granting access to functions in the applications.
The following diagram illustrates the concepts of roles and groups in Anzo:
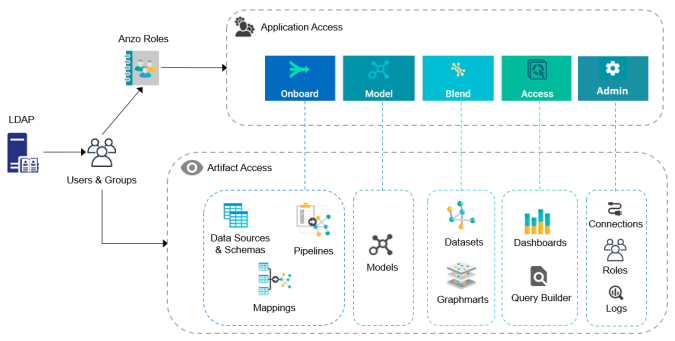
A user's role determines whether they can access the Onboard menu and create a new Data Source or see the Blend menu and create a new Graphmart. But their group assignment determines whether they can view, modify, or delete Data Source and Graphmart artifacts that are created by other users.
For more information about leveraging a directory server and details about users, groups, and roles see the sections below.
Leveraging a Directory Server (LDAP)
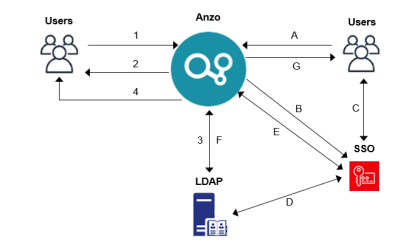
Anzo can be configured to access your directory server via Direct Authorization or Single Sign-On (SSO). The diagram below shows the procedures that are followed for both methods. The left side of the diagram (the numbered steps) shows the direct authorization method. The right side of the diagram (the lettered steps) shows the SSO method. The table below the diagram describes the processes for each method.
| Direct Authorization | Single Sign-On |
|---|---|
|
|
For more information on connecting to a directory server, see the following topics:
Users and Groups
Groups typically originate in a directory server and are synced to Anzo. However, you can also create custom groups that are internal to Anzo. Typically users also originate from the directory server, but you can create user accounts in Anzo. Any users and groups that are created in Anzo are stored in Anzo's internal LDAP server.
For information about retrieving user and groups from the directory server or creating internal Anzo users, see the following topics:
Roles
Anzo is configured with predefined roles. You can create new roles and disregard the predefined roles, remove the predefined roles, or add your groups to the predefined roles and modify the assigned permissions as needed.
For details about the default roles and instructions on creating new roles, see the following topics:
Permissions
The way you give a role access to the Anzo applications and particular functions in those applications is to assign permissions to the role. All permissions are predefined in Anzo. Custom permissions cannot be created, and the predefined permissions cannot be deleted.
For details about all of the permissions, see the following topic:
For an overview of the data access management concepts, see Artifact Access Control Concepts.