Graphmart, Data Layer, and Step Sharing
Graphmart sharing is managed by configuring user and group permissions at the graphmart, data layer, and step level. Together, the permissions defined for each graphmart component control the data that a user can access, whether they can view or modify a component, and whether they can view or modify a component's metadata.
This topic provides details about the permissions for each graphmart component and includes instructions for configuring permissions for each type of component.
Graphmart, Layer, and Step Permissions Reference
In the Anzo application, graphmarts, data layers, and steps offer the same predefined permission sets to apply and use the same mechanism for assigning permissions, but the privileges granted with a permission set differ depending on the component:
- Graphmart permissions control a user’s ability to activate, deactivate, and reload or refresh a graphmart, view or modify a graphmart and its metadata, and view, create, or modify data layers.
- Data Layer permissions control which users can access or modify the data that is output from a layer, i.e., which users can enable or disable layers, edit, create, and delete layers, or change layer metadata, such as security settings.
- Step permissions also control which users can access or modify the data that is output from a layer, i.e., which users can enable and disable steps, add, edit, and delete steps, and view or modify step metadata.
This section provides information about the predefined permission sets and default permissions for each component.
- Permission Inheritance
- Graphmart Level Permissions Reference
- Data Layer Level Permissions Reference
- Step Level Permissions Reference
Permission Inheritance
When assigning permissions at the graphmart, data layer, or step level, you can configure that component to inherit the permissions from another component or pass on its permissions to other components. For example, you can configure one graphmart to pass its permissions to other graphmarts. Inheritance transmits all of the artifact's permissions for all users and groups.
By default, data layers and steps inherit their permissions from the parent graphmart. That means graphmart permissions supersede the permissions set at the data layer or step level by default. For simplicity and to avoid unexpected outcomes, Cambridge Semantics recommends that you manage all permissions at the graphmart level.
The inheritance settings are displayed below the permissions table on the graphmart Sharing tab or the Security tab for data layers and steps.
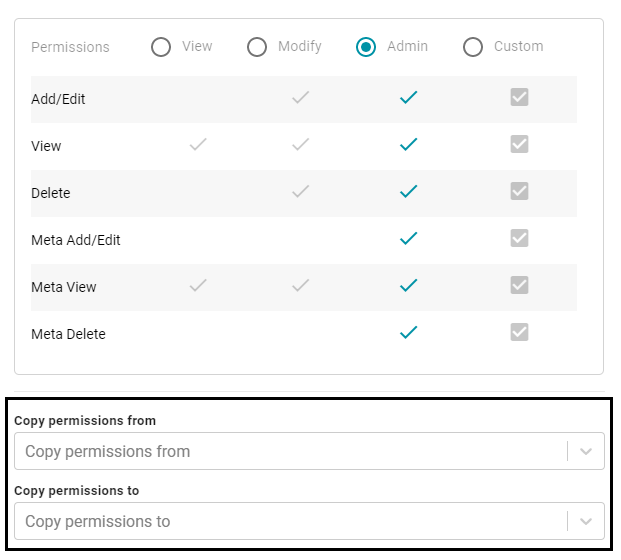
Since graphmarts pass permissions to layers and steps, by default, the Copy permissions from field is empty for graphmarts. And the Copy permissions to field is populated with the names of the data layers and steps in the graphmart. For data layer and step permissions, the Copy permissions from field is populated with the parent graphmart name, and the Copy permissions to field is empty.
Graphmart Level Permissions Reference
Graphmart level permissions control a user’s ability to view, activate and deactivate, reload or refresh a graphmart, modify a graphmart's content, or view or modify its metadata. There are three predefined graphmart permission sets that include a combination of six permissions that can be assigned to user or group. You also have the option to customize the set of permissions that are applied to a user or group.
The table below lists the predefined permission sets and describes the privileges that are granted for each permission that is part of the predefined set:
| Set | Permission | Allows a user to: |
|---|---|---|
| View | View (Graphmart) |
|
| Meta View (Sharing Tab) |
|
|
| Modify | In addition to the View and Meta View permissions described above, the Modify set includes the Add/Edit and Delete permissions described below. | |
| Add/Edit (Graphmart) |
|
|
| Delete (Graphmart) |
|
|
| Admin | In addition to the View, Meta View, Add/Edit, and Delete permissions described above, the Admin set includes the Meta Add/Edit and Meta Delete permissions described below. | |
| Meta Add/Edit (Sharing Tab) |
|
|
| Meta Delete (Sharing Tab) |
|
|
Default Graphmart Permissions
The table below lists the predefined permission sets that are applied by default when a new graphmart is created. Besides the sysadmin user, the graphmart creator is granted Admin privileges by default. The Everyone role is granted View privileges by default. No other users or groups have graphmart permissions assigned by default.
| Anzo User/Role | Applied Permission Set |
|---|---|
| Sysadmin User | Admin |
| Graphmart Creator | Admin |
| Everyone Role | View |
The default graphmart permission configuration is controlled by the default access policy for the Graphmarts registry. For information about default access policies, see Managing Default Access Policies.
Data Layer Level Permissions Reference
Data layer level permissions control a user’s ability to view, enable and disable, and edit, create, and delete a data layer or view or modify its metadata.
Data layer permissions also depend on the permissions assigned for the parent graphmart. By default, all data layers and steps in a graphmart inherit their permissions from the graphmart. To navigate to a data layer, a user needs to have View permissions for the parent graphmart. To activate or deactivate the graphmart that contains the data layer of interest, or to create a new data layer, a user needs Modify permissions for the graphmart.
There are three predefined data layer permission sets that include a combination of six permissions that can be assigned to an Anzo user, group, or role. You also have the option to customize the set of permissions that are applied to a user or group.
The table below lists the predefined permission sets and describes the privileges that are granted for each permission that is part of the predefined set:
| Set | Permission | Allows a user to: |
|---|---|---|
| View | View (Data Layer) |
|
| Meta View (Security Tab) |
|
|
| Modify | In addition to the View and Meta View permissions described above, the Modify set includes the Add/Edit and Delete permissions described below. | |
| Add/Edit (Data Layer) |
|
|
| Delete (Data Layer) |
|
|
| Admin | In addition to the View, Meta View, Add/Edit, and Delete permissions described above, the Admin set includes the Meta Add/Edit and Meta Delete permissions described below. | |
| Meta Add/Edit (Security Tab) |
|
|
| Meta Delete (Security Tab) |
|
|
Default Data Layer Permissions
The table below lists the predefined permission sets that are applied by default when a new layer is created. Besides the sysadmin user, the layer creator is granted Admin privileges by default. The Everyone role is granted View privileges by default. No other users, groups, or roles have layer permissions assigned by default.
| Anzo User/Role | Applied Permission Set |
|---|---|
| Sysadmin User | Admin |
| Layer Creator | Admin |
| Everyone Role | View |
Step Level Permissions Reference
Step level permissions control a user’s ability to view, enable and disable, and edit, create, and delete a step or view or modify its metadata.
Step level permissions also depend on the permissions assigned for the parent data layer and graphmart. By default, all data layers and steps in a graphmart inherit their permissions from the graphmart. To navigate to a step, a user needs to have View permissions for the parent graphmart and layer. To enable, disable, or edit and delete steps, a user needs Modify permissions for the data layer.
There are three predefined step permission sets that include a combination of six permissions that can be assigned to an Anzo user, group, or role. You also have the option to customize the set of permissions that are applied to a user, group, or role.
The table below lists the predefined permission sets and describes the privileges that are granted for each permission that is part of the predefined set:
| Set | Permission | Allows a user to: |
|---|---|---|
| View | View (Step) |
|
| Meta View (Security Tab) |
|
|
| Modify | In addition to the View and Meta View permissions described above, the Modify set includes the Add/Edit and Delete permissions described below. | |
| Add/Edit (Step) |
|
|
| Delete (Step) |
|
|
| Admin | In addition to the View, Meta View, Add/Edit, and Delete permissions described above, the Admin set includes the Meta Add/Edit and Meta Delete permissions described below. | |
| Meta Add/Edit (Security Tab) |
|
|
| Meta Delete (Security Tab) |
|
|
Default Step Permissions
The table below lists the predefined permission sets that are applied by default when a new step is created. Besides the sysadmin user, the step creator is granted Admin privileges by default. The Everyone role is granted View privileges by default. No other users, groups, or roles have step permissions assigned by default.
| Anzo User/Role | Applied Permission Set |
|---|---|
| Sysadmin User | Admin |
| Step Creator | Admin |
| Everyone Role | View |
Configuring Graphmart, Layer, or Step Permissions
Follow the instructions below to configure permissions at the graphmart, data layer, or step level. For details about the predefined permission sets and associated privileges, see the Graphmart, Layer, and Step Permissions Reference above.
- In the Anzo application, expand the Blend menu and click Graphmarts. Anzo displays a list of the existing graphmarts. For example:
- On the Graphmarts screen, click the name of the graphmart for which you want to configure permissions. Anzo displays the graphmart details. For example:
- Follow the appropriate instructions below, depending on whether you want to configure permissions at the graphmart level or for a layer or step in the graphmart:
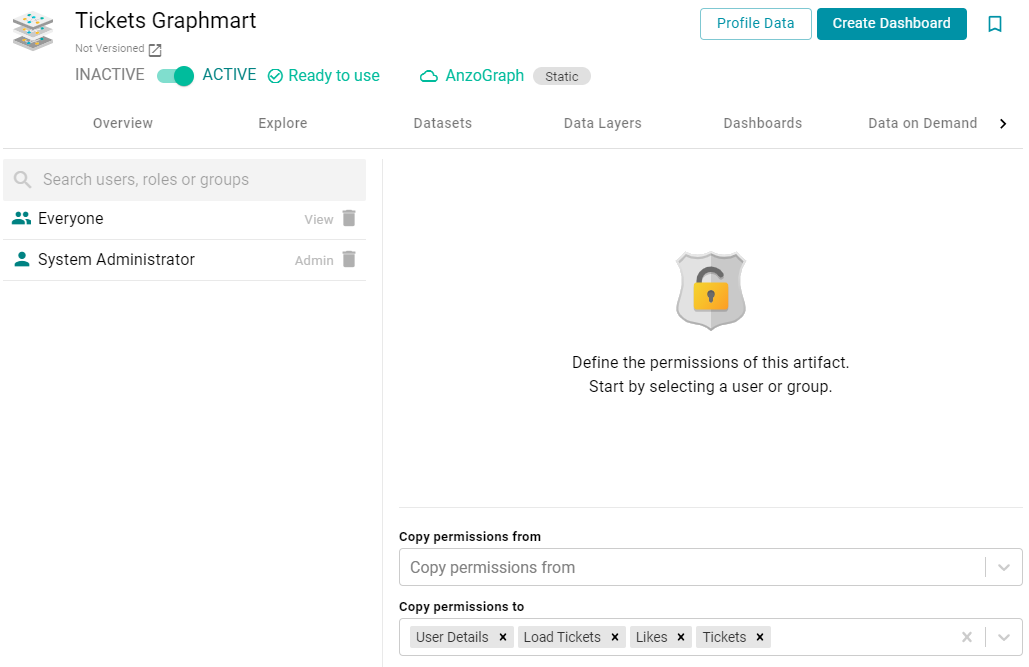
- To configure permissions at the graphmart level, click the Sharing tab. The Sharing screen is displayed. For example:
- To configure permissions for a data layer or step in the graphmart, click the Data Layers tab. On the Data Layers screen, find the layer or step that you want to configure. Then click the menu icon (
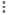 ) for that layer or step and select Edit. On the Edit screen, click the Security tab. The security screen is displayed. For example:
) for that layer or step and select Edit. On the Edit screen, click the Security tab. The security screen is displayed. For example: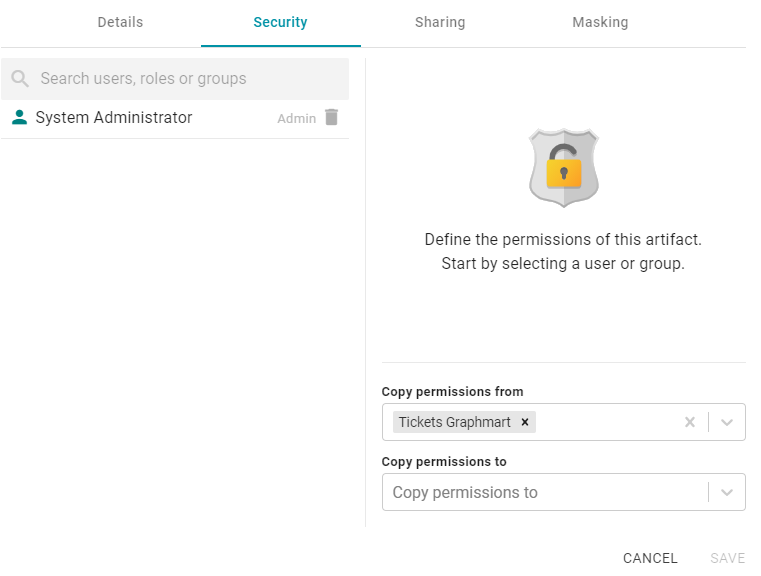
- To configure permissions at the graphmart level, click the Sharing tab. The Sharing screen is displayed. For example:
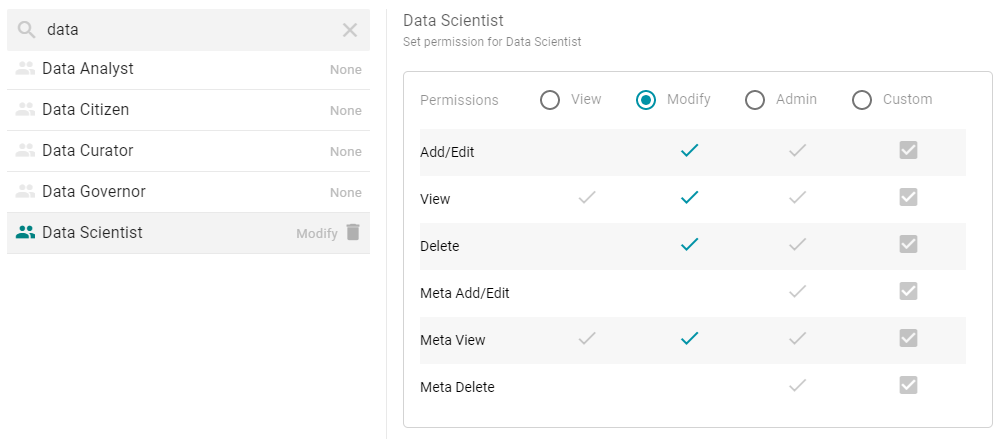
- On the security screen, type a value in the Search users, roles or groups field to find and display a user or group. The resulting list shows the current permission level that is set for each user or group that was found by the search. For example, the image below shows a list of roles and their current permissions (None):
- On the left side of the screen, select the user or group for which you want to configure permissions. The permissions settings are displayed on the right side of the screen. For example:
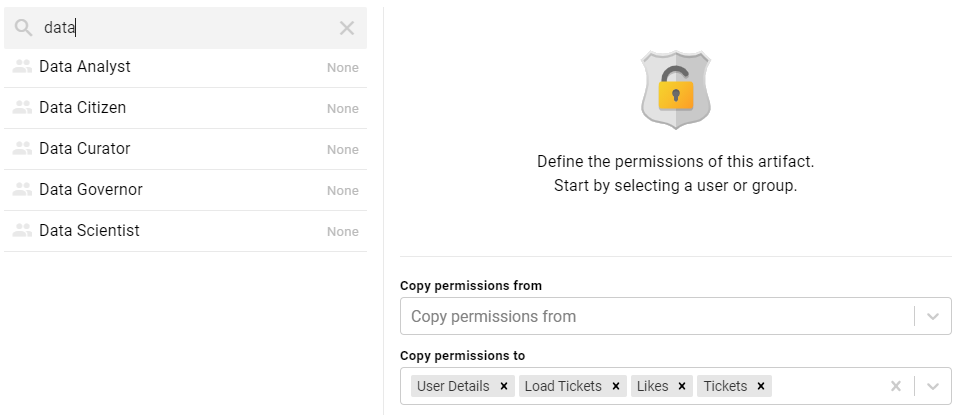
- To assign a predefined set of permissions, click the View, Modify, or Admin radio button to assign that level of access to the selected user, role, or group. Refer to the Graphmart, Layer, and Step Permissions Reference above for details about the permissions sets. For example, the image below gives Modify permissions to users with the Data Scientist role:
If you want to customize the permissions, click the Custom radio button and then select or deselect the permissions checkboxes. To clear permissions for a user, role, or group, click the trashcan icon (
 ) next to the user, role, or group name.
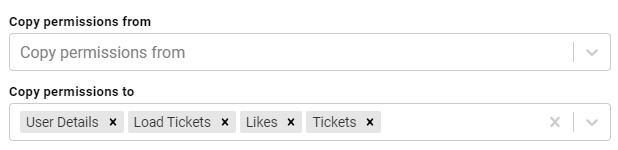
) next to the user, role, or group name. - If you want to change the inheritance for the component, use the fields below the permissions table. For details about inheritance, see Permission Inheritance above. To apply all of the permissions from another component to this component, select the component to inherit from in the Copy permissions from field. To pass this component's permissions to other components, select the components to pass permissions to in the Copy permissions to field. For example, the image below shows the inheritance configuration for a graphmart:
Changes to graphmart, data layer, and step permissions take effect immediately. Users do not need to log out and log back in, and affected graphmarts do not need to be reloaded or refreshed.